Verizon DBIR 2020 - Brief Analysis
Verizon releases Data Breach Investigations Report every year. It has recently released the latest report which is a result of 81 contributing organizations and it reviews 32,002 security incidents and 3,950 breaches that occured in 2019.
This post is a short analysis of some interesting observations from the report, regarding breaches and methods used by the actors.
 |
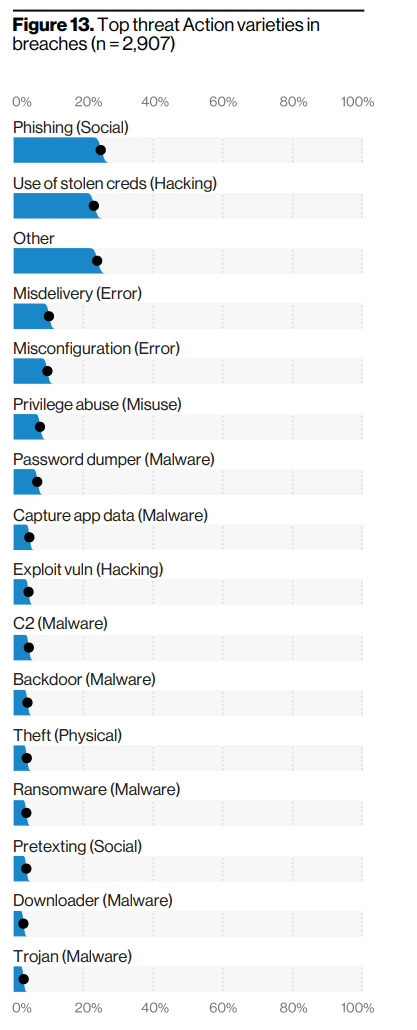 |
This figure show that more than 70% of all the data breaches resulted from attacks like phishing, use of stolen credentials and errors. More complicated attacks like using malware or exploiting vulnerabilities has contributed to only 20% of the breaches.
Social Attacks
While it doen’t appear as threatening as malware or hacking, social attacks (phishing) prove that they are even more dangerous than the rest. 96% of phishig is carried out via emails and only 3% via websites. Most of these phishing attacks compromise credentials, personal, internal, medical and bank information. Data breach at BenifitMall, Indiana healtcare group and Colarado based healtcare facility breach are some notable ones. A good sign is that the click rates in phishing campaigns have reduced from 25% in 2012 to 3.4%
Hacking
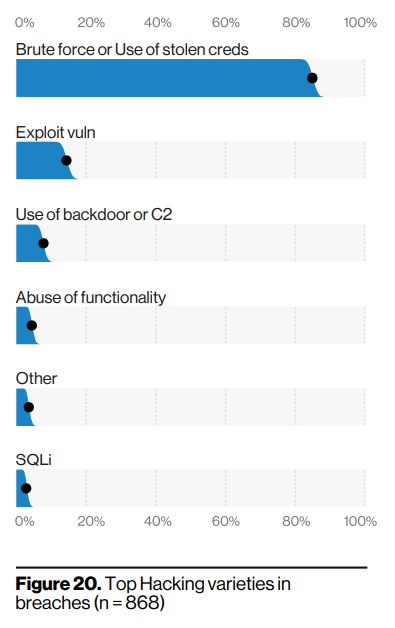
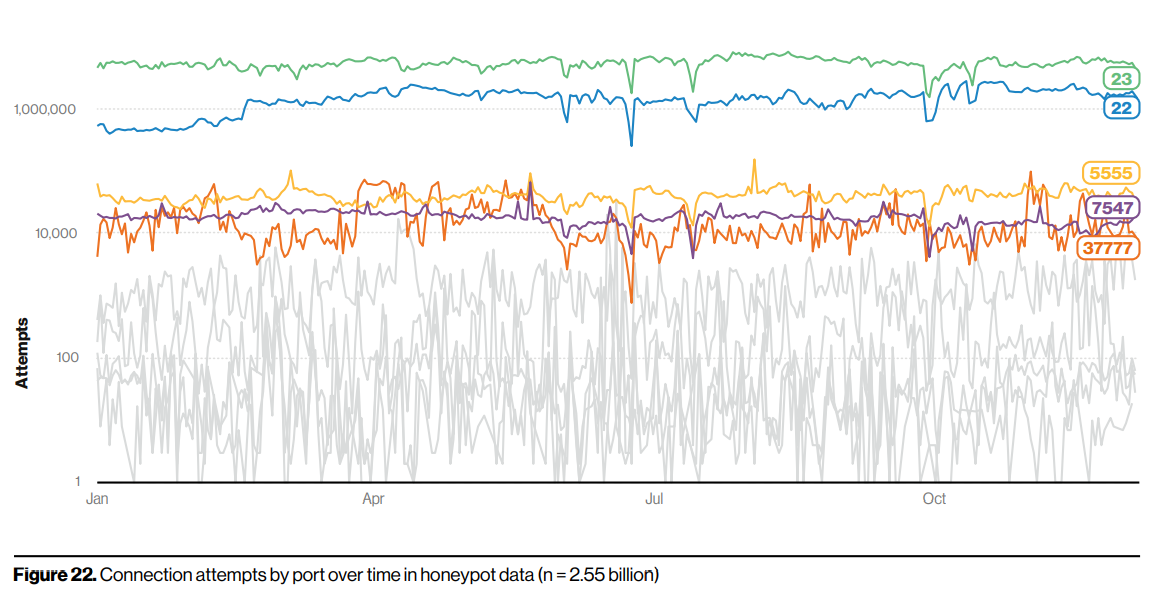
Brute forcing and credential stuffing (use of stolen credentials) contributes 80% of the breaches by hacking. Per year, an organization records 1000 to a billion attempts of credential stuffing attempts. This makes it very important to have multi factor authentication implemented by organizations and more importantly, users need to use different passwords for accounts on different sites or use password managers to create unique passwords and store them. Credential stuffing is a continuous campaign and with every data breach, hackers just update their dictionaries with latest credentials and continue the attacks. Although there are firewalls and other detection and mitigation systems implemented, hackers use botnets at a scale of thousands of devices to carry out such attacks. Apart from web applications, credential attempts over time are in the order of millions for ports 23 (telnet) and port 22 (ssh), followed by high ports 5555 (usually listened by android debug bridge), 7457 (listened by TR-069 protocol used by modems) and port 37777 (used by DVRs and CCTV cameras). The best way to use ssh is with a private key, removing the usage of password.
Traditional hacking like exploiting vulnerabilities, abusing functionality, SQLI, use of backdoors (associated with more advanced threats) contribute to 20% of the breaches. About 90% of all these breaches are based on web applications. Even though there are a lot of vulnerabilities discovered every year, a very small percentage of them are used in breaches. This has been the case in the last few years as well. But this doesn’t mean the vulnerable software can go unpatched. They lead to more serious problems like malware/ portential for APTs.
Errors
While the percentage of breaches due to hacking, social and malware are decreasing over the last few years, breaches due to errors are consistently increasing. They are now equally as common as social breaches and more common than malware breaches. Most of these errors are due to misconfigurations, which has more than doubled over the years. This could be due to the increase in security researchers and other third parties finding such incidents. A lot of such misconfigurations occur while using cloud services. Unprotected databases, un encrypted storage buckets, unrestricting firewalls are a few of such misconfigurations. The Capital One breach, data breach at Imperva and Century Link breach are some good examples of breaches due to misconfiguration.
Malware
Malware contributed to 17% of the breaches, which has reduced from 28% last year. As the other attack types like hacking and social breaches benifit from the theft of credentials, it is no longer necessary for the threat actors to add malware in order to maintain persistence. Similar to phishing, the most of the breaches due to malware are targeted at obtaining credentials. Most malware is delivered via email and are often embedded in office documents and windows apps. Shell scripts, archives, android apps and dlls are few other file types used to embed malware. Surprisingly, ransomware contributes to only 20% of breaches due to malware.

Leave a comment